Wireless Sniffing Campus Network Authentication Gateway (IPGW)
大家都知道, On April 18, the login interface of a certain school’s campus network was upgraded. I will talk about the specific changes in the next article. For most people, the process of entering the user name and password to log in has not changed. But for the rabbit, this means that some dark things can secretly open a small window to see the sun.
In this article, only one proof-of-concept , does not provide specific attack tools, nor does it provide step-by-step penetration tutorials, and I am too lazy to explain the principles. The practice of hiding good things is not my original creation.
In fact, it is very easy. Use any tool to capture packets first. Rabbits are not good at learning. They can only capture unencrypted Wi-Fi data packets, which will be enough. It should be noted that some network cards of the Intel series cannot enable the monitor mode. What are the specific ones? some. 😌
So which network cards can do bad things? The model number is not indicated here. Taobao search for “network card” will mainly show chips from the R family and another R family, both of which are acceptable. B’s is also available, and to be more precise, all Apple notebooks are available. There is also the A family, which is the wireless chip in the TP-LINK router that everyone is familiar with. After flashing the firmware, you can enable monitoring, and you can even remotely sniff… But then again, why spend so much effort to buy a MacBook~
The old version of IPGW is said to be made by the teacher of the network center himself (you can also see how concise the concise version is…), in short, one cannot be separated, the core is a http form, there are two inputs inside, click a button to submit, it is easy to write an interface that can be written in five minutes.
The network operation that occurs after clicking the connect button is extracted into a curl command in Chrome like this {% codeblock lang:sh %}curl -m 2 ‘http://202.118.1.95/ipgw/ipgw.ipgw’
-H ‘Origin:http://ipgw.neu.edu.cn’ -H ‘Accept-Encoding: gzip, deflate’ -H “User-Agent:$UA” -H ‘Content-Type: application/x-www-form-urlencoded’ -H ‘Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8’ -H ‘Cache-Control: max-age=0’ -H ‘Referer: http://ipgw.neu.edu.cn/basic.html' -H ‘Host: ipgw.neu.edu.cn’ -H ‘Connection: keep-alive’ --data “uid=$ 1&password=$2&operation=$COMMAND&range=2&timeout=1”
{% endcodeblock %} where, -H All headers can be ignored, the important part is the parameters in POST DATA, uid username, password is the password, command It is an operation, which can be connecting or disconnecting this computer or disconnecting all links of this account. All these parts are in the network, that is, on NEU_ send in plaintext _ of! That is, click** connect ** In the future, your username and password will be broadcast to all the places where your mobile phone signal reaches. Now, that’s why we can do bad things.
The packet capture process has been skipped (it can’t be reproduced anyway), and here we use the cap packet as a souvenir for demonstration.
When capturing packets in Wi-Fi, the most troublesome thing is piles of beacon packets and piles of tcp retransmissions. First filter them all out, and the end is like this.
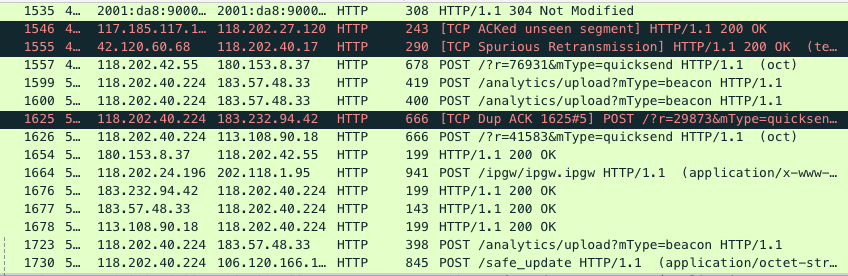
This makes it clear at a glance that what we are looking for is a package that sends a POST request to /ipgw.ipgw. Tuli happens to be there.
Then we click on it, and we can see some information about the owner of the package in the picture.
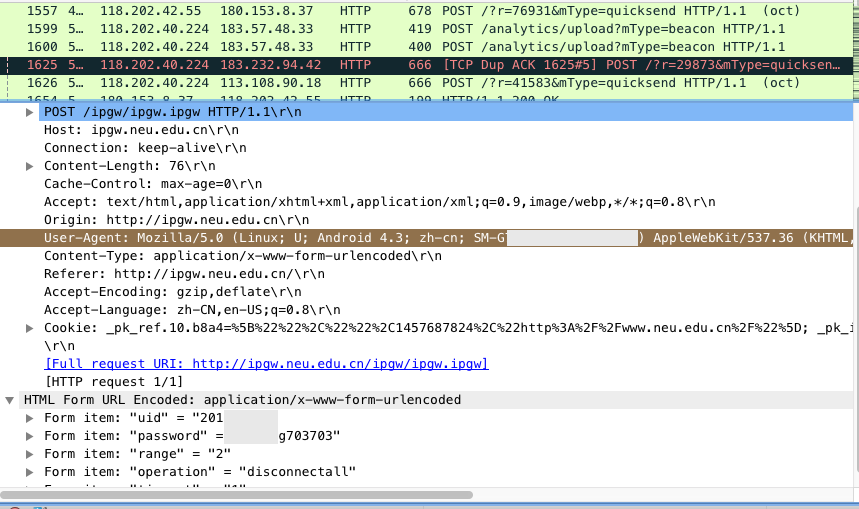
- Android, Android 4.3
- Samsung handphone
- Username Password
- is using the regular version instead of the lite version of the gateway
- I may feel that someone is on his account, so I choose to disconnect
That’s all. It’s nothing but packet capture. In fact, it’s so simple that there is only a little threshold for knowing that there is such a thing (in fact, many black technologies only have such a threshold…), but it’s terrible to use, ready-made things, ready-made tool.
Alas, the person who appeared on the picture is still a classmate of our class… When I caught this password (mainly because the pinyin of the name is still in the password), I told him anonymously on Ma Huateng that his password was leaked , Ma Liu changed it. And now, ipgw has been replaced with a new one, and his password is still there, and it has not changed.
How to prevent it?
Well, the big characters are more eye-catching. It’s actually quite simple,
It turns out that when surfing the Internet, you will type in the browser,
http://ipgw.neu.edu.cn
Now just replace it with
https://ipgw.neu.edu.cn
make one more s ** It won't be exhausting! **
Um? Who asked why there is an extra s?
Have you learned cryptography and cybernetics?
回去重修!
In the next article, I will write a little more about how to automate the entire sniffing process, and it will involve changes in the new version of IPGW, and… why should I write these shameful things. Stay tunedˊ_>ˋ